In this article, we will understand what is hash function in blockchain technology and why it is used. We shall also cover the basics of the hash function and its important characteristics for blockchain. Finally, we will see practical examples of the SHA-256 hash function which is used in bitcoin blockchains.
Contents
What is Hash Function?
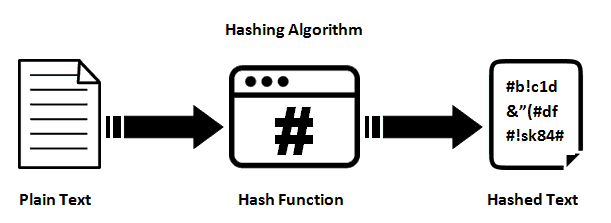
The concept of hash function comes from the field of Cryptography that is used to generate fixed-length output from any arbitrary long input that can be string or numbers or alphanumeric.
Hash functions are keyless and are commonly used for digital signatures and message authentication codes. There are various families of hash functions, the popular ones are as follows-
- MD
- SHA1
- SHA-2
- SHA-3
- RIPEMD
- Whirlpool
What is Hash Function in Blockchain
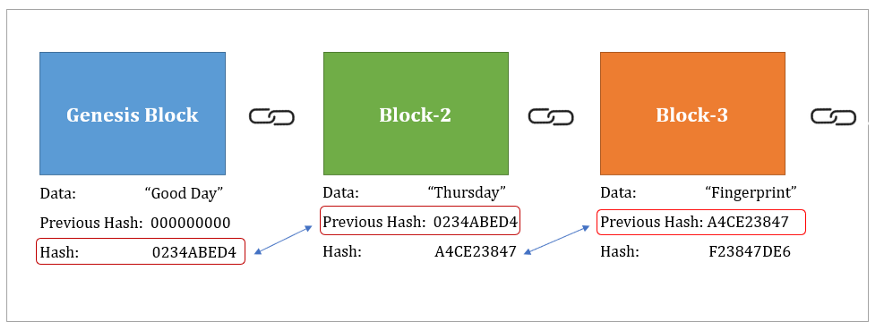
In blockchain technology, the hash function is used to generate the hash for a particular block that serves as a unique fingerprint for identifying the block. Each block stores the hash value of the previous block, thus forming the chain. It should be noted that the first block which is called the genesis block obviously does not point to any previous hash.
Hash is generated by using the data of the block and the nonce value as input. The process of generating the hash of the block is what essentially miners do when they mine blockchains like Bitcoins and Ethereum.
Bitcoins use the SHA-256 hash function which belongs to the SHA-2 family whereas Ethereum uses the Keccak hash function.
Why Hash Function is used in Blockchain
The hash function has certain characteristics that make it a good choice to complement the fundamental requirements of blockchains.
1. Pre Image Resistance or One Way
This means the hash produced by the hash function cannot be reversed engineered to produce the original input value. Let us understand this with the below equation –
h(x) = y
If h is the hash function and x is the input data and y is the hash, then under no circumstances one should be able to derive x from y. This is the pre-image resistance or one-way property. This is important in blockchain to prevent hackers from exploiting the hash value for any malicious intent.
2. Second Pre Image Resistance or Weak Collision Resistance
This property says that it should be almost impossible to create another different input that can create a hash value that originally belongs to another input. Let us understand this with the below equation.
h(x) = y
Given that for an input x, the hash function h produces hash y. Now it should be practically impossible to create another input z (where z is not equal x) such that h(z) = y.
This is very significant from the blockchain perspective, otherwise, it would have allowed hackers to update the data on a block in such a way that its hash does not change.
3. Deterministic
This property ensures that for any given input the hash function should always produce the same hash value.
h(x) = y
This means h(x) should always produce y for the input value of x and not any other output no matter how many times h(x) is used. This deterministic property helps other miners in the blockchain network to verify the hash value of a particular block produced by a miner before adding that block throughout the network.
4. Fast computation
The hash functions are easy and fast to compute the hash value regardless of the input message size. This is very important for blockchain because the miners compute millions and billions of hash per second and a fast hash function prevents any bottleneck in the network.
5. Avalanche Effect
The term avalanche effect means here that even one bit change in input brings an avalanche of changes in the computation of hash. As a result, instead of changing slightly the new hash is entirely new compared to the previous one.
This property ensures that the mathematical puzzle of finding the right hash does not become very predictable for miners where they start tweaking the nonce value minutely to reach the target on a predictable path.
Practical Example of Hash Function
There is a very good website https://andersbrownworth.com/blockchain/hash to practically understand the working of the SHA-256 hash function.
You will find a field to input the data and it will automatically calculate the hash for it. For our example, we gave details of the three transactions that produced a specific hash for it. Now if you delete the data field and again give the same transaction it will again produce the same hash, which highlights its deterministic nature.

Next, we change the second transaction details from $50 to $500 acting like a hacker. But it produces a new hash that is completely different from the above hash, due to the avalanche effect that we discussed earlier.
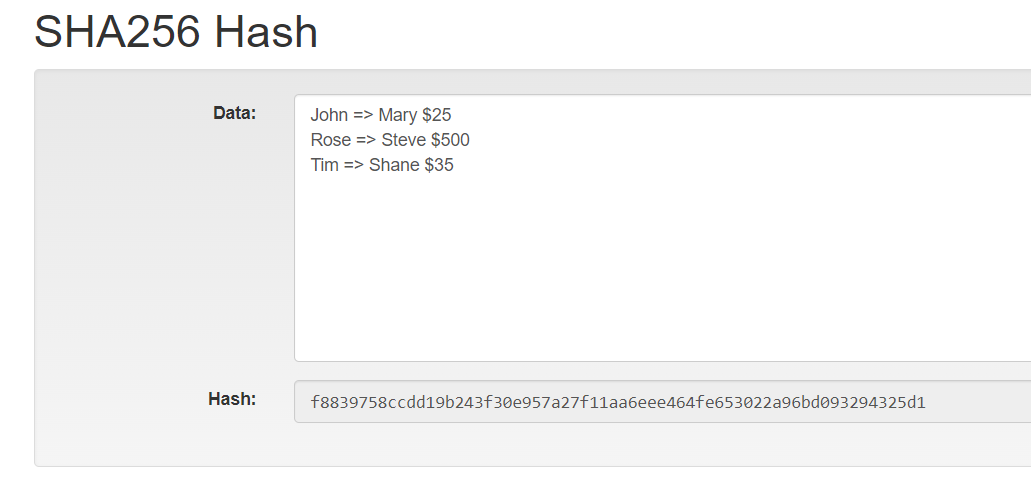
We encourage you to use this website to interact with the SHA-254 hash function and practically understand it with your own examples.

